

With cyberattacks and the skills gap getting worse, SOCs can no longer afford to have analysts manually coordinate contextual data. D3’s integration with Recorded Future enables automated enrichment of Smart SOAR incidents with precision SecOps intelligence for rapid assessment of threats.
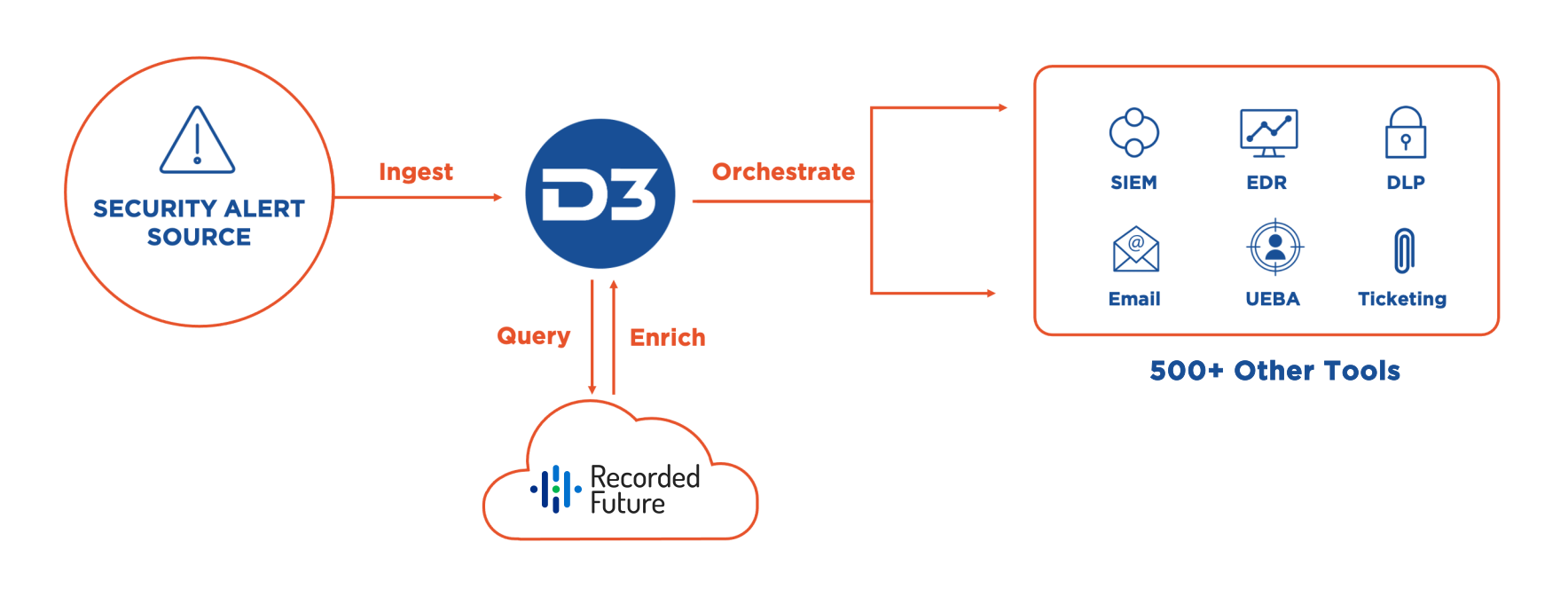
Our Connected SOAR Security Alliance brings hundreds of vendors together, allowing customers to benefit from our deep industry relationships and fully vendor-agnostic, independent SOAR platform.